Application
Security
Protect your applications from threats with our advanced solutions.


Application
Security
Protect your applications from threats with our advanced solutions.







Application
Security
Protect your applications from threats with our advanced solutions.
Beyond the Code:
Elevating Application Security to an Art Form
In the age of digital transformation, safeguarding your software is no longer optional—it’s essential. At Desert Sentinel Solutions, we don’t just identify vulnerabilities, we build fortresses. Our multi-layered approach integrates Application Security Testing (AST) right into your development workflow, scrutinizes third-party libraries, and ensures you’re shielded from the latest threats.
From static and dynamic testing to architectural threat modeling, we employ cutting-edge technologies and strategies to make sure your applications aren’t just efficient—they’re impenetrable.

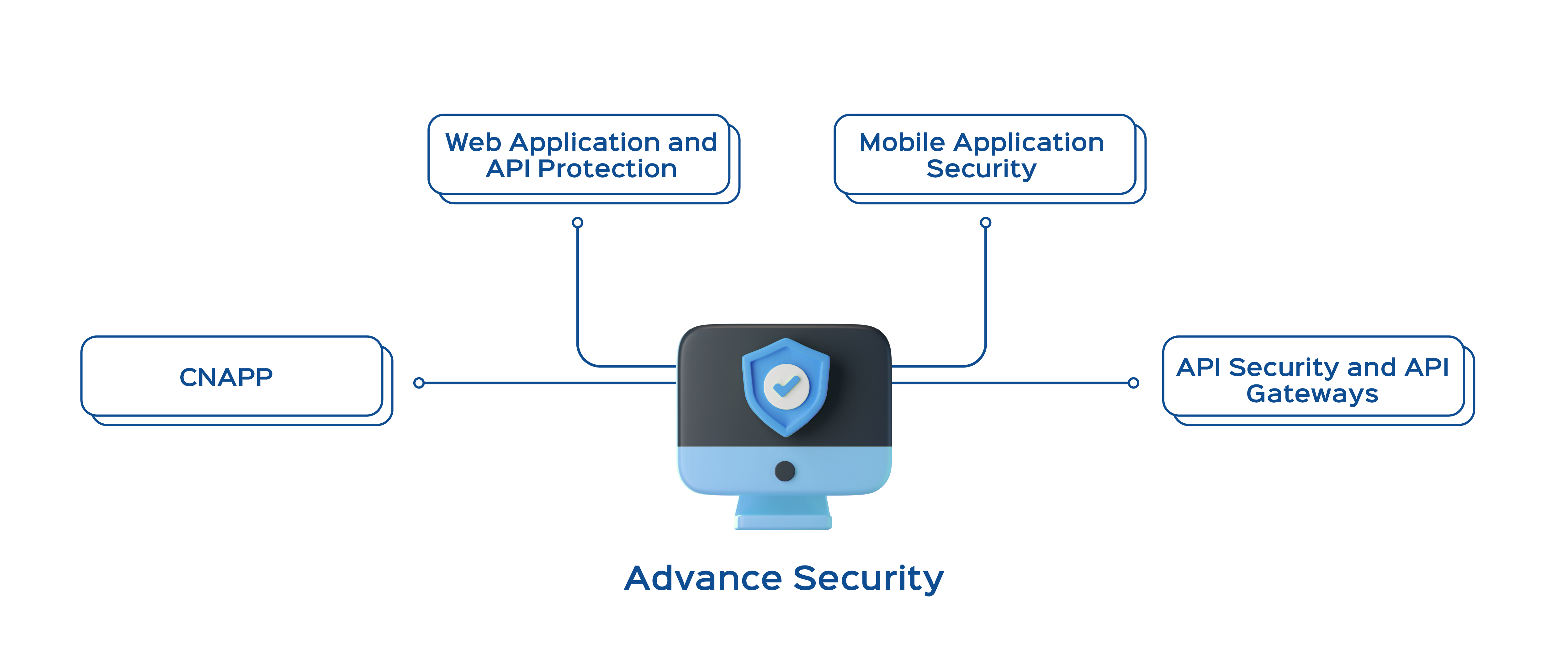
What Sets Us Apart in Application Security
Integrated Testing
Workflows
Seamlessly integrating Application Security Testing (AST) into your development process for real-time vulnerability management.

Cutting-Edge
Technology
Employing the latest in static, dynamic, and interactive testing tools to ensure your applications are rigorously checked against all forms of threats.
Comprehensive Threat Modeling
We don't just look at the code; we look at the architecture, implementing threat modeling to identify potential weaknesses before they become a problem.

Third-Party
Library Scrutiny
Never let a third-party library be your weakest link. We vet every external codebase your application relies on.

Adaptive Security
Measures
Our security measures evolve with the threat landscape, always keeping you one step ahead of potential attackers.

Cloud-Native to
On-Premise Flexibility
Whether your application resides in the cloud or on-premise, we offer tailored security solutions that fit your unique needs.
Integrated Testing
Workflows
Seamlessly integrating Application Security Testing (AST) into your development process for real-time vulnerability management.

Cutting-Edge
Technology
Employing the latest in static, dynamic, and interactive testing tools to ensure your applications are rigorously checked against all forms of threats.

Comprehensive Threat
Modeling
We don't just look at the code; we look at the architecture, implementing threat modeling to identify potential weaknesses before they become a problem.

Third-Party
Library Scrutiny
Never let a third-party library be your weakest link. We vet every external codebase your application relies on.

Adaptive Security
Measures
Our security measures evolve with the threat landscape, always keeping you one step ahead of potential attackers.

Cloud-Native to
On-Premise Flexibility
Whether your application resides in the cloud or on-premise, we offer tailored security solutions that fit your unique needs.
Ready to Fortify Your Business?
Our Security Success by the Numbers
Metrics That Matter
Networks
Compliance Score
Response Time
Monitored Daily
Secured
Rate
Rate
Rate
Vulnerabilities
Rate
Satisfied Clients, Secured Networks:
Our Success Stories
Satisfied Clients, Secured Networks:
Our Success Stories
Securing Your Digital Future
Knowledge Hub
Multi-Factor Authentication, or MFA, has become one of the most widely recommended cybersecurity defenses in the world. But despite being...
Just like washing your hands prevents infections, cyber hygiene protects your systems from digital threats. It’s not flashy, it’s not...
In the cybersecurity world, “testing” your defenses is non-negotiable. But not all tests are created equal. Two terms that often...
If your organization has employees, devices, data, or internet access — you need a cybersecurity policy. It doesn’t matter if...




