





SkyHigh Security: Elevate Your Cloud Capabilities with Unmatched Protection
In the cloud, it’s not just about storage and scalability, it’s about unassailable security. At Gulf Sentry Services, we go beyond the basics to offer you a comprehensive cloud security strategy, tailor-made to fit your specific needs. From leveraging cloud-native features to integrating cutting-edge Cloud Access Security Brokers (CASBs), we make your cloud environment a vault that is both functional and secure.
Step into the future of Cloud Security Posture Management (CSPM) and Workload Protection—elevate your cloud, elevate your business.

Basic and Advance
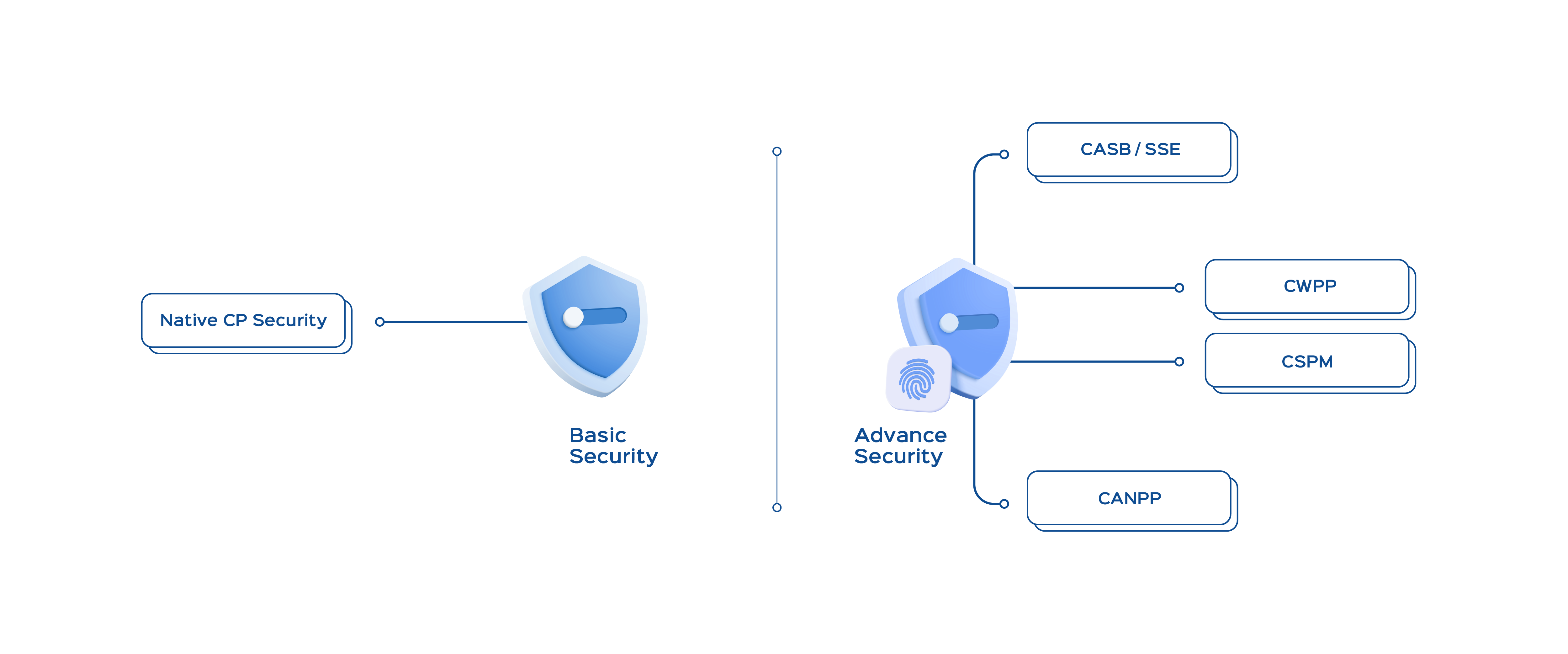
What Sets Us Apart in Cloud Security

Tailor-Made
Strategies
No two clouds are the same; that's why we design bespoke security frameworks that fit your unique needs.

Advanced CASB
Integration
Utilize our expertise in Cloud Access Security Brokers to make data in your cloud apps as secure as a vault.
Multi-Cloud
Mastery
Whether it's AWS, Azure, or Google Cloud, we offer nuanced solutions for every platform.

CSPM
Excellence
Stay ahead of vulnerabilities with our cutting-edge Cloud Security Posture Management services, making your cloud infrastructure virtually unassailable.

Workload-Centric
Protection
We employ specialized tools to give you unprecedented control and visibility over your cloud workloads.

Future-Proof
Solutions
Our cloud security measures are scalable, adaptable, and designed to evolve with emerging technologies.

Tailor-Made
Strategies
No two clouds are the same; that's why we design bespoke security frameworks that fit your unique needs.

Advanced CASB
Integration
Utilize our expertise in Cloud Access Security Brokers to make data in your cloud apps as secure as a vault.

Multi-Cloud
Mastery
Whether it's AWS, Azure, or Google Cloud, we offer nuanced solutions for every platform.

CSPM
Excellence
Stay ahead of vulnerabilities with our cutting-edge Cloud Security Posture Management services, making your cloud infrastructure virtually unassailable.

Future-Proof
Solutions
Our cloud security measures are scalable, adaptable, and designed to evolve with emerging technologies.

Workload-Centric
Protection
We employ specialized tools to give you unprecedented control and visibility over your cloud workloads.
Ready to Fortify Your Business?
Our Security Success by the Numbers
Metrics That Matter
Networks
Compliance Score
Response Time
Monitored Daily
Secured
Rate
Rate
Rate
Vulnerabilities
Rate
Satisfied Clients, Secured Networks:
Our Success Stories
Satisfied Clients, Secured Networks:
Our Success Stories
Securing Your Digital Future
Knowledge Hub
Multi-Factor Authentication, or MFA, has become one of the most widely recommended cybersecurity defenses in the world. But despite being...
Just like washing your hands prevents infections, cyber hygiene protects your systems from digital threats. It’s not flashy, it’s not...
In the cybersecurity world, “testing” your defenses is non-negotiable. But not all tests are created equal. Two terms that often...
If your organization has employees, devices, data, or internet access — you need a cybersecurity policy. It doesn’t matter if...




