




Guardians of Your Data: Navigating Complex Data Landscapes with Precision and Integrity
In an age where data is the new gold, safeguarding it is not just an option—it’s a necessity. At Desert Sentinel Solutions, we revolutionize the way you perceive and protect data. Leveraging a data-centric security architecture, we offer bespoke control mechanisms that can be universally applied across all your data silos and applications.
It’s more than just protection; it’s about empowering you to use your data to its full potential while staying compliant and risk-free. With us, your data isn’t just stored—it’s fortified.

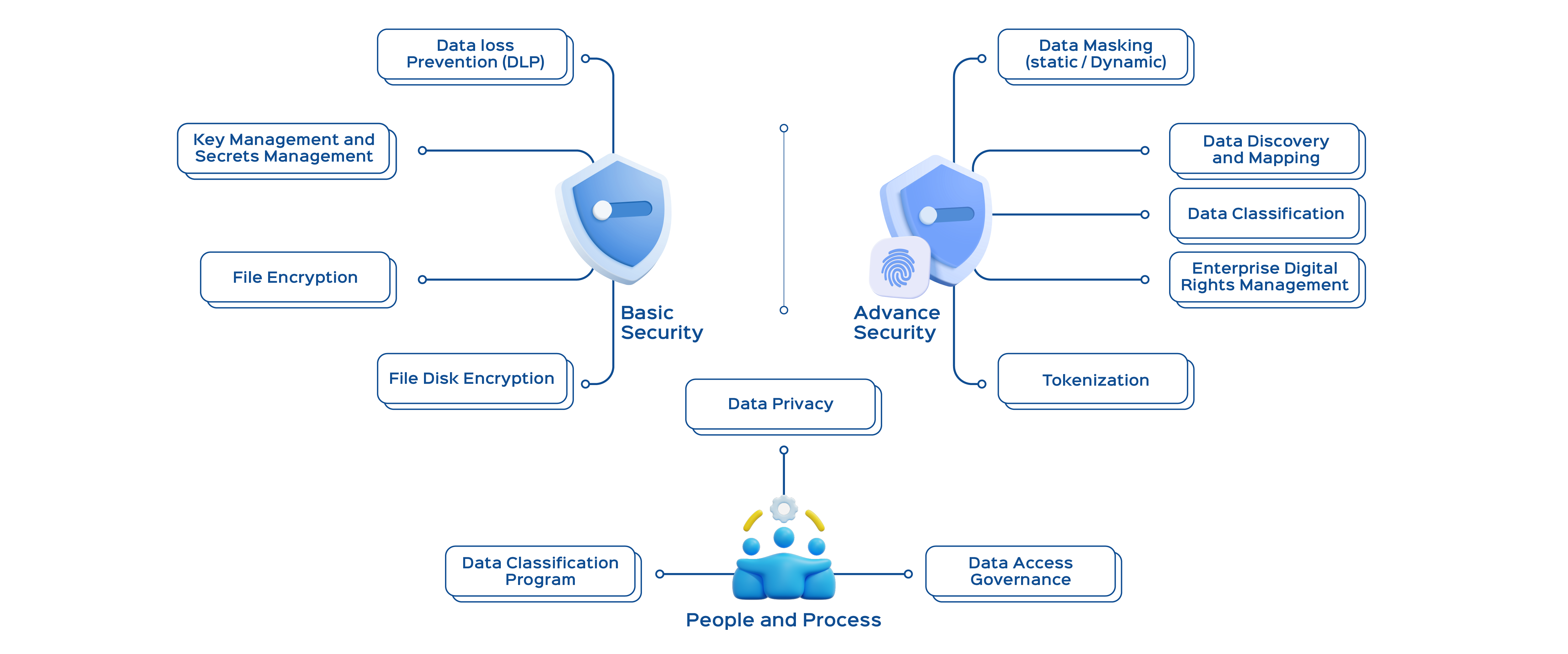
What Sets Us Apart in Data Security

Future-Proof
Security
In an ever-changing digital landscape, our data security solutions are designed to adapt and evolve, providing you long-term peace of mind.

Data-Centric
Approach
We don't just look at where your data is stored; we consider how it is used, ensuring multi-dimensional protection.

Legal & Regulatory
Mastery
Navigate the maze of compliance with ease, as our solutions are engineered to meet the most stringent legal requirements.

Risk-Adaptive
Solutions
Our security measures evolve with the threat landscape, always keeping you one step ahead of potential attackers.

Cloud-to-Edge
Protection
Whether your data is in the cloud or on-premises, our security coverage is all-encompassing.

Operational
Efficiency
We balance security and usability, ensuring that your operations are never hindered by excessive controls.

Data-Centric
Approach
We don't just look at where your data is stored, we consider how it is used, ensuring multi-dimensional protection.

Legal & Regulatory
Mastery
Navigate the maze of compliance with ease, as our solutions are engineered to meet the most stringent legal requirements.

Risk-Adaptive
Solutions
Our security measures evolve with the threat landscape, always keeping you one step ahead of potential attackers.

Cloud-to-Edge
Protection
Whether your data is in the cloud or on-premises, our security coverage is all-encompassing.

Operational
Efficiency
We balance security and usability, ensuring that your operations are never hindered by excessive controls.

Future-Proof
Security
In an ever-changing digital landscape, our data security solutions are designed to adapt and evolve, providing you long-term peace of mind
Ready to Fortify Your Business?
Our Security Success by the Numbers
Metrics That Matter
Networks
Compliance Score
Response Time
Monitored Daily
Secured
Rate
Rate
Rate
Vulnerabilities
Rate
Satisfied Clients, Secured Networks:
Our Success Stories
Satisfied Clients, Secured Networks:
Our Success Stories
Securing Your Digital Future
Knowledge Hub
Multi-Factor Authentication, or MFA, has become one of the most widely recommended cybersecurity defenses in the world. But despite being...
Just like washing your hands prevents infections, cyber hygiene protects your systems from digital threats. It’s not flashy, it’s not...
In the cybersecurity world, “testing” your defenses is non-negotiable. But not all tests are created equal. Two terms that often...
If your organization has employees, devices, data, or internet access — you need a cybersecurity policy. It doesn’t matter if...




