




Building Digital Fortresses: Transforming Infrastructure Security in an Unpredictable World
Your digital infrastructure is the backbone of your business. At Desert Sentinel Solutions, we don’t just safeguard it—we architect it to be unassailable. Whether you’re combating business email compromise, sophisticated malware, or data theft, our multi-layered security approach leverages the latest in DevSecOps, cloud workload protection, and specialized DNS tools to bring you peace of mind.
Our tailored solutions seamlessly integrate with your existing infrastructure, turning your technology ecosystem into a synchronized, fortified environment.

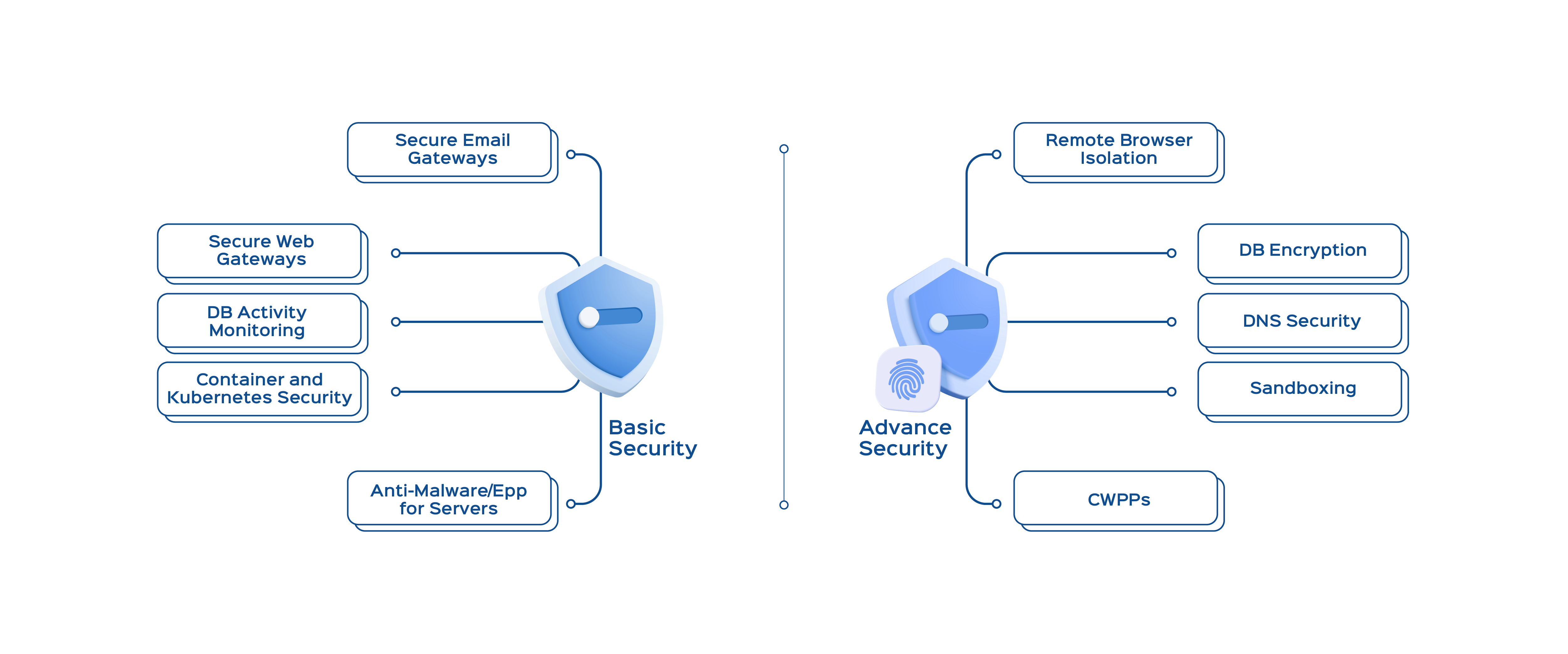
What Sets Us Apart in Infrastructure Security

DevSecOps
Integration
Seamlessly incorporate security measures into your DevOps process for streamlined operations and enhanced protection.

Adaptive Cloud
Protection
Specialized security measures for your cloud-based assets, from simple data storage to complex multi-cluster Kubernetes environments.

DNS
Excellence
Advanced DNS solutions that offer traffic confidentiality and secure your overall network infrastructure.

Tailored Security
Architecture
A multi-layered security model that is designed to meet the unique challenges and risks your organization faces.

Synchronized
Defense
Our solutions effortlessly align with your existing systems to create a holistic, unified security framework.

Future
Ready
Anticipate tomorrow's threats today with our adaptive, scalable security solutions designed for long-term resilience.

DevSecOps
Integration
Seamlessly incorporate security measures into your DevOps process for streamlined operations and enhanced protection.

Adaptive Cloud
Protection
Specialized security measures for your cloud-based assets, from simple data storage to complex multi-cluster Kubernetes environments.

DNS
Excellence
Advanced DNS solutions that offer traffic confidentiality and secure your overall network infrastructure.

Tailored Security
Architecture
A multi-layered security model that is designed to meet the unique challenges and risks your organization faces.

Synchronized
Defense
Our solutions effortlessly align with your existing systems to create a holistic, unified security framework.

Future
Ready
Anticipate tomorrow's threats today with our adaptive, scalable security solutions designed for long-term resilience.
Ready to Fortify Your Business?
Our Security Success by the Numbers
Metrics That Matter
Networks
Compliance Score
Response Time
Monitored Daily
Secured
Rate
Rate
Rate
Vulnerabilities
Rate
Satisfied Clients, Secured Networks:
Our Success Stories
Satisfied Clients, Secured Networks:
Our Success Stories
Securing Your Digital Future
Knowledge Hub
Multi-Factor Authentication, or MFA, has become one of the most widely recommended cybersecurity defenses in the world. But despite being...
Just like washing your hands prevents infections, cyber hygiene protects your systems from digital threats. It’s not flashy, it’s not...
In the cybersecurity world, “testing” your defenses is non-negotiable. But not all tests are created equal. Two terms that often...
If your organization has employees, devices, data, or internet access — you need a cybersecurity policy. It doesn’t matter if...




