




Guarding Your Digital Frontier: Redefining Network Security Services for the Modern Age
At Desert Sentinel Solutions, we believe that a secure network isn’t just about preventing access, it’s about granting it wisely. Our zero-trust security architectures don’t just fortify your network—they transform it into an impenetrable digital fortress that protects data and applications at every turn.
We bring a holistic approach to network security, offering systems that integrate seamlessly with your existing tools and providing the kind of visibility and control that doesn’t just manage risks—it eliminates them. From static and dynamic testing to architectural threat modeling, we employ cutting-edge technologies and strategies to make sure your applications aren’t just efficient—they’re impenetrable.

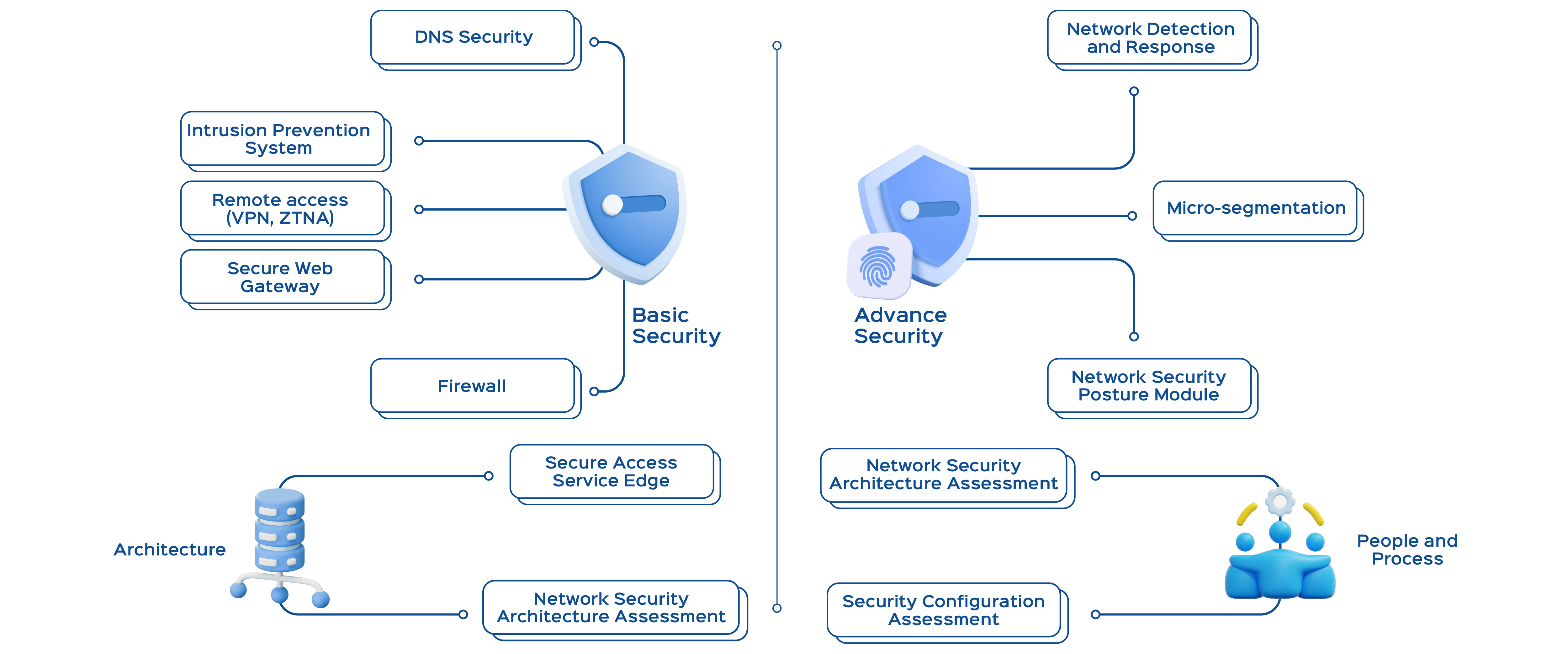
What Sets Us Apart in Network Security

Innovative Policy Enforcement
We go beyond generic rule sets to develop customized policies that suit your business requirements while upholding the highest security standards.

Seamless
Integration
Our solutions aren't just top-of-the-line; they integrate flawlessly with your existing platforms and tools.

Holistic Risk
Management
We don't just identify vulnerabilities; we provide comprehensive solutions that mitigate risks at every layer of your network.

Data-Centric
Protection
It's not just about securing your network; it's about safeguarding your data across all its touchpoints.

Advanced Threat
Visibility
We offer systems that not only detect threats but provide actionable insights for rapid response and prevention.

Custom-Built
Solutions
No two networks are the same, which is why our services are tailored to fit your specific operational needs and security goals.

Seamless
Integration
Our solutions aren't just top-of-the-line; they integrate flawlessly with your existing platforms and tools.

Holistic Risk
Management
We don't just identify vulnerabilities; we provide comprehensive solutions that mitigate risks at every layer of your network.

Data-Centric
Protection
It's not just about securing your network; it's about safeguarding your data across all its touchpoints.

Advanced Threat
Visibility
We offer systems that not only detect threats but provide actionable insights for rapid response and prevention.

Custom-Built
Solutions
No two networks are the same, which is why our services are tailored to fit your specific operational needs and security goals.

Innovative Policy Enforcement
We go beyond generic rule sets to develop customized policies that suit your business requirements while upholding the highest security standards.
Ready to Fortify Your Business?
Our Security Success by the Numbers
Metrics That Matter
Networks
Compliance Score
Response Time
Monitored Daily
Secured
Rate
Rate
Rate
Vulnerabilities
Rate
Satisfied Clients, Secured Networks:
Our Success Stories
Satisfied Clients, Secured Networks:
Our Success Stories
Securing Your Digital Future
Knowledge Hub
Multi-Factor Authentication, or MFA, has become one of the most widely recommended cybersecurity defenses in the world. But despite being...
Just like washing your hands prevents infections, cyber hygiene protects your systems from digital threats. It’s not flashy, it’s not...
In the cybersecurity world, “testing” your defenses is non-negotiable. But not all tests are created equal. Two terms that often...
If your organization has employees, devices, data, or internet access — you need a cybersecurity policy. It doesn’t matter if...




